IID, Incident Information Detection Sytem
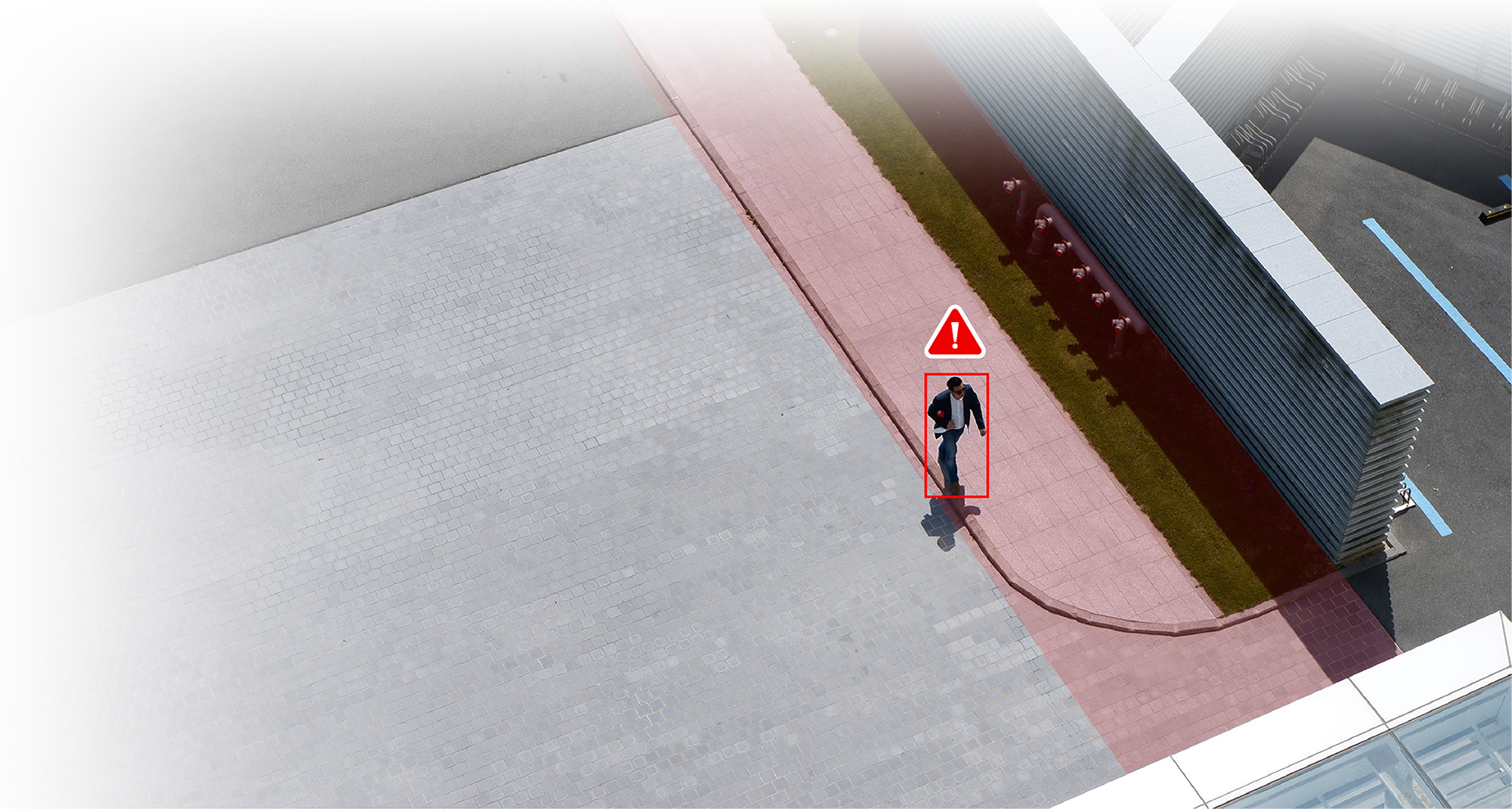
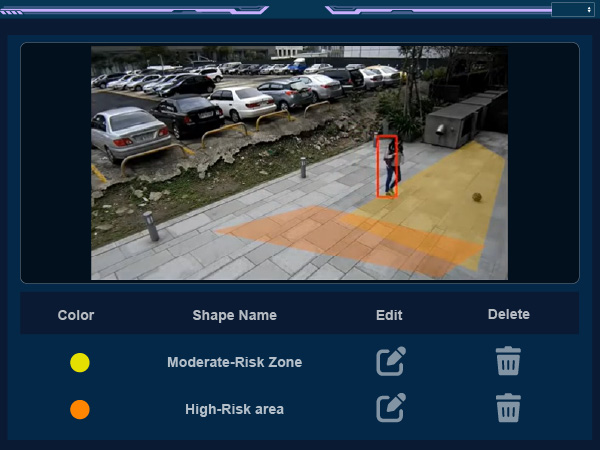
The IID (Incident Information Detection) system is an AI-powered intelligent security solution for high-security environments. It uses artificial intelligence and advanced image analysis to establish virtual electronic perimeters. These perimeters detect, identify, and track people or vehicles even without physical barriers.
With deep learning and multi-object tracking technology, IID precisely distinguishes between different object types. It automatically identifies abnormal behaviors, such as unauthorized entry, prolonged loitering, or suspicious object placement.
The IID system provides real-time alerts. It integrates seamlessly with alarm systems, access control, and central monitoring platforms. This creates a comprehensive security protection network.
It is widely used in airports, seaports, military bases, industrial parks, logistics centers, and large event venues. The system offers intrusion prevention, event tracking, behavior analytics, and decision-making support for security management.
The system operates reliably in all weather conditions. It remains stable at night, in rain, fog, or complex lighting. IID delivers high accuracy, real-time response, and scalable intelligence. This makes it an essential part of modern smart security infrastructure.